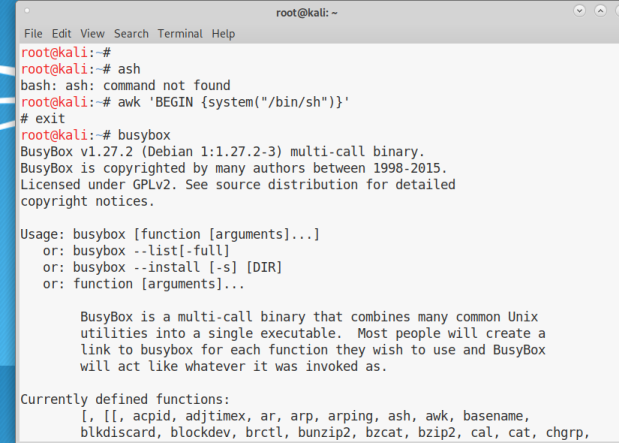
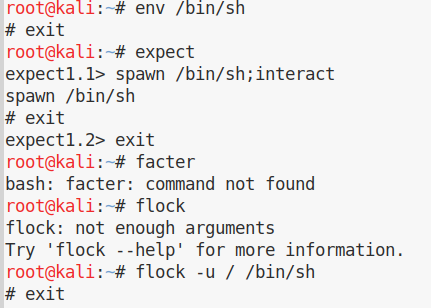
So Usually while solving CTF or doing some pentesting project you stuck on getting a shell because of some restricted shell environment or some detection tools.
While searching on this topic I came to this amazing link https://gtfobins.github.io/#+shell
The list on the website contains an awesome comprehensive list of some daily or uncommon bin exe which can help you to break free restriction in restricted environments. Usage of the Environment variable and how to elevate privilege is also mentioned out there. Few of the binary usages are quite uncommon could easily be used for malicious purposes. All n all a great information.
I tried my hands on a few of them.