I visited Germany and here are some pics for my own remembrance.








I visited Germany and here are some pics for my own remembrance.








I started cooking when I moved to Hyderabad. It has been a great experience cooking I always wanted to cook since my childhood. So finally got the opportunity to work on this skill as I was in a new place new opportunities just found me.
When I first tried cooking I always felt that there is oil left in my food. Then I understood the process and chemistry of cooking oil with veggies. Then the best taste comes up on its own.
I will be still watching courses and other things on cooking and learning more as this is a life skill. Despite gender, everyone should know how to cook basic meals.
Cooking is just another section of chemistry. That’s it
I will post more on this.
How to get Visa: IVP (Israel visa processing) is a service provider for the State of Israel, authorized to provide support services to visa applicants in India. Visit this site https://www.israelvisa.in/ to get more details on Visa process.
There are two types of Visa submission:
a. Normal: minimum 5 working days – Rs 3330
b. Fast track: minimum 2 working days – Rs 7650
You need to submit application form (not hand written) and other required documents to IVP Center of your respective location.
Use below link to access the application form
https://www.israelvisa.in/online-visa-application-form/b2-tourist-visa
Use below link to know details of required documents
Track your visa application status by using below link
https://www.israelvisa.in/track-your-application
Hotel Booking
Check hotel rating on Booking.com and book using Agoda.com. Always use free cancellation type to book hotel. Agoda has zero cancellation policies which you can avail.
Tel Aviv Hotel: Abraham Hotel, Guest Kitchen is available
Jerusalem Hotel: Abraham Hotel and Kalpan Hotel, Guest Kitchen is available
Flight Booking
For Visa, always use dummy tickets for flight booking and book confirmed tickets once you get your visa. You can use below link to book dummy flight tickets:
dummyticket.com

Some want to go to the US, Some want to Go to Europe, Some want to go to Canada, I just wanted to see my favorite country Israel which has stood up against all the adversaries via their courage, knowledge, and Here I am at the western wall






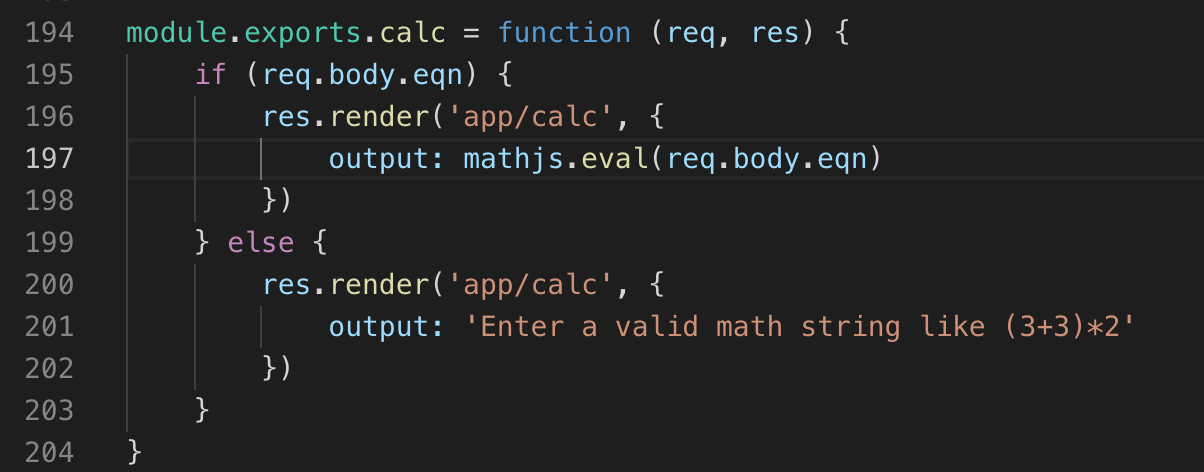
The following small code of python grabs all the inputs from the html page or templates in a project and gives you a clear picture to attack and fuzz.
The project used for this experiment https://github.com/CSPF-Founder/JavaVulnerableLab
Here is the code for this:
Post related to it will be posted very soon

So I have taken this challenge and hope I code something cool and code.Mostly I will be coding about security.
So The program for today is a simple one, During incident response and forensic we need check for the persistence of malicious software in case of mac malware they use launch Agent and Launch Daemons .The plist files which contains information on how to run a program is found on these locations.

Sometimes the plist.info file is binary format .We can use plutil to convert into xml and vice-versa.
import os
from pathlib import Path
def crawlAgentsAndDaemons():
agentsNDaeomns={
str(Path.home())+'/Library/LaunchAgents':['Currently logged in user'],
'/Library/LaunchAgents':['Currently logged in user'],
'/Library/LaunchDaemons':['root or the user specified with the key UserName'],
'/System/Library/LaunchAgents':['Currently logged in user'],
'/System/Library/LaunchDaemons':['root or the user specified with the key UserName']
}
directories=list(agentsNDaeomns.keys())
for dirs in directories:
print ("============"+dirs+"===========")
print ()
plistFiles=os.listdir(dirs)
for pfiles in plistFiles:
print ("Application Name: "+pfiles)
print()
fileOpen=open(dirs+'/'+pfiles)
try:
fileRead=fileOpen.read()
print(fileRead)
fileOpen.close()
except(UnicodeDecodeError):
try:
os.system('plutil -convert xml1 '+dirs+'/'+pfiles)
fileOpen=open(dirs+'/'+pfiles)
fileRead=fileOpen.read()
print(fileRead)
fileOpen.close()
os.system('plutil -convert binary1 '+dirs+'/'+pfiles)
except:
pass
crawlAgentsAndDaemons()
sudo python inspectmacosxlaunchagentanddaemon.py > dump.txtafter running this program we get application details like this and can check for malicious program by checking program’s arguments.


So I m just started to work on JS animation I don’t know I should call it only js animation as lots of CSS is also involved but fuck it lets just write some code.
Before I present you the code you must visit this timing function reference on w3school and experiment with them and get yourself comfortable.
https://www.w3schools.com/js/js_timing.asp
https://www.w3schools.com/howto/howto_js_typewriter.asp
The code is here https://gist.github.com/MohitDabas/f9a99c16fc54a09200beb065db0d0418

Before you start reading this I want to make sure the whole project is based upon this grep command.



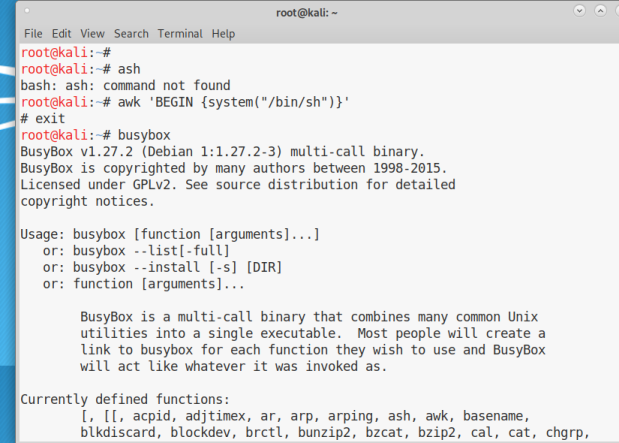
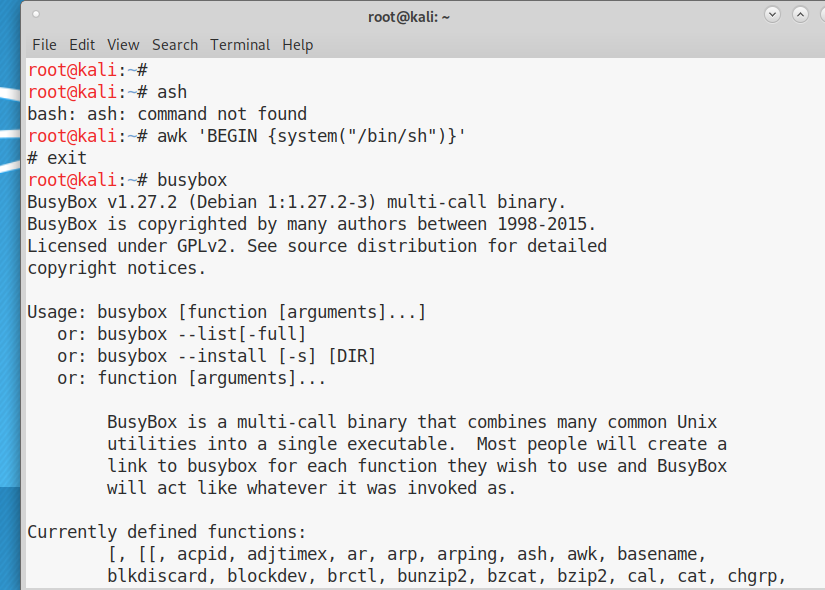
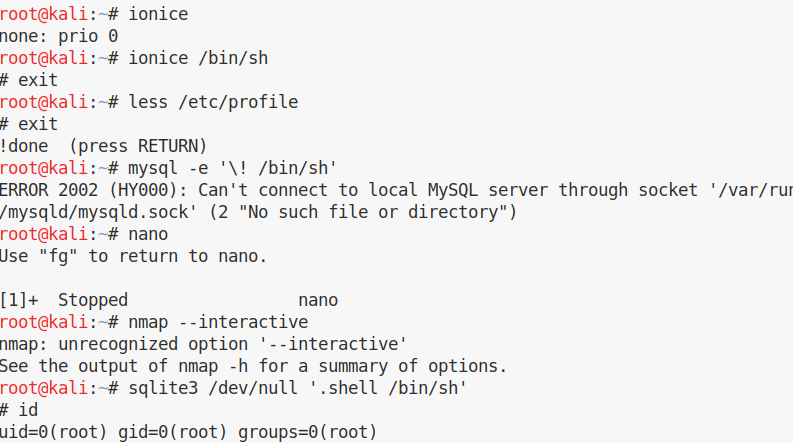
So Usually while solving CTF or doing some pentesting project you stuck on getting a shell because of some restricted shell environment or some detection tools.
While searching on this topic I came to this amazing link https://gtfobins.github.io/#+shell
The list on the website contains an awesome comprehensive list of some daily or uncommon bin exe which can help you to break free restriction in restricted environments. Usage of the Environment variable and how to elevate privilege is also mentioned out there. Few of the binary usages are quite uncommon could easily be used for malicious purposes. All n all a great information.
I tried my hands on a few of them.